3 minutes
Volatility autoruns plugin
Finding persistence points (also called Auto-Start Extensibility Points, or ASEPs) is a recurring task of any investigation potentially involving malware.
Checking for persistence is relatively easy when you have a forensic copy of the
hard-drive: tools such as
Sysinternal’s Autoruns
(and its lesser-known ability to analyze offline systems by manually selecting
registry hives) or
regripper and its
user_run and soft_run plugins all do the job perfectly.
When all you have is a live memory dump and your trusty Volatility framework,
things get a little more tedious since you have to play around with printkey
to display every possible Run or Service key. The svcscan plugin can come in
handy but it won’t tell you which DLL the service is hosting or when was the
service created.
Plugin features
To make an analyst’s life a bit easier, I came up with the autoruns plugin.
autoruns basically automates most of the tasks you would need to run when
trying to find out where malware is persisting from. Once all the autostart
locations are found, they are matched with running processes in memory.
Today, the plugin goes through:
- Popular keys in the HKLM and HKCU hives (Run, RunOnce, etc.). This is the most common place for malware to establish persistence in.
- Winlogon parameters (such as
ShellandUserinit) and Notify registrations - Services: It will go through all services that are set to automatically start
with Windows. If the service is invoked through
svchost.exe, it will grab the loaded DLL name. - AppInit DLLs: The DLLs specified here are loaded with every application that is ran on the system.
- Scheduled tasks in memory (tested on Windows 7 only)
Besides listing all these persistence points and their corresponding values, the plugin will match them with a running process. This is particularly useful to:
- Immediately identify the process that corresponds to the service that loaded a suspicious-looking DLL.
- Determine which binaries where set to load at system start and are no longer running. Malware often injects itself into other processes before exiting, so an entry with no associated PIDs may be an indicator of strange activity.
How-to
The plugin is pretty straightforward to use. The folder where the plugin is
located should be passed on to Volatility using the --plugins= parameter.
Relevant options for the plugin are:
-vor--verbose- Shows extra information that would normally be filtered (like Services from theSystem32folder)-tor--asep-type- Use it to focus on specific ASEPS. Options are:autoruns,services,appinit,winlogon, andtasks. You can specify any combination of them with a comma-separated list:autoruns,services. Leave blank to get all ASEPs.--output=[text|table]-tablewill output the text in a table format (less readable but somehow more consice; see screenshot below). The default output mode istext, where more information is avialable.
Sample plugin output:
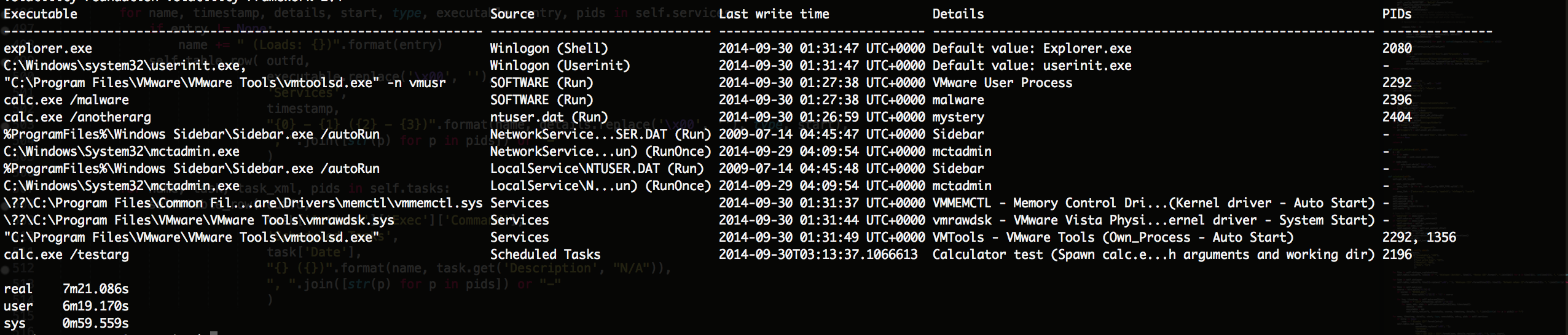
Roadmap
I plan on including some more ASEPs like Scheduled tasks (done!) and Startup folders. If you see any other way than going through the MFT, please do let me know!
I also plan on extending support to OS X and hopefully Linux.
Since the plugin needs to parse a lot of registry keys, it can take a while to run (it took approximately 3 minutes to do all the checks on the memory sample I tested it on).
Details and download
The plugin has its own GitHub repo. Check the README there for more details on the specific checks that are made.
It was tested with Volatility 2.4 on several of the memory samples available here.